REVEAL Wi-Fi NETWORK PASSWORDS WITH WirelessKeyView


As students flock back to the library and the rest of us head back to the coffee shop for a warm drink and free Wi-Fi, the safety and security of our laptops—and all of the important and sensitive information they hold—are of the utmost importance. Let’s take a look at several free and cheap methods you can (and should) use to keep your laptop safe, secure, and out of the hands of thieves. We’ll also take a look at software that tracks and even snaps pictures of the thief in the event he did get away with your precious gear.
 They aren’t free, but an inexpensive laptop lock can do wonders for securing your laptop and deterring thieves. You can find a huge range of laptop locks on Amazon ranging from $12 to $40, and whether you know it or not almost all laptops support them. They’re relatively inexpensive, and for the price they’re an excellent deterrent. After all, if you were a thief scoping out two laptops—one with a lock and one without—which which would you go for?
They aren’t free, but an inexpensive laptop lock can do wonders for securing your laptop and deterring thieves. You can find a huge range of laptop locks on Amazon ranging from $12 to $40, and whether you know it or not almost all laptops support them. They’re relatively inexpensive, and for the price they’re an excellent deterrent. After all, if you were a thief scoping out two laptops—one with a lock and one without—which which would you go for?
You’ve got your laptop physically locked down, so you’re off to a great start. For phase two of your laptop security system, try setting up a software-based security system and alarm. Here’s how they work. Say you get up from your seat for a minute but you want an added layer of protection on top of your laptop lock. Car alarm-like applications for your laptop let you walk away for a moment without breaking down your whole work area and packing up your laptop. The benefit of an alarm in a crowded library or coffee shop is that all eyes are on your laptop and the potential thief when it goes off. An alarm is a second phase deterrent if a potential thief still goes after your laptop despite your lock.  For Windows users, free application Laptop Alarm (original post) will sound an alarm whenever anyone unplugs the power cable, the mouse is moved or unplugged, or the laptop is shut down. It’s a very simple application that could use some improvements (especially compared to the Mac alternative below), but it’s not bad for what it does. Mac users, try the nearly identical applications iAlertU or Lockdown (original post). (Lockdown is based on the open-source iAlertU.) You can arm and disarm both applications car-alarm style with your Apple Remote, and both use the motion detection system in any newer MacBook to set off the alarm if someone moves your laptop. The alarm also sounds with any movement of your mouse, keyboard activity, and more. Whenever the alarm is triggered, your MacBook’s iSight camera snaps a picture and can send it to any email address. Alternately, you can also automatically upload iAlertU pics to your FTP server if you’d prefer that to email.
For Windows users, free application Laptop Alarm (original post) will sound an alarm whenever anyone unplugs the power cable, the mouse is moved or unplugged, or the laptop is shut down. It’s a very simple application that could use some improvements (especially compared to the Mac alternative below), but it’s not bad for what it does. Mac users, try the nearly identical applications iAlertU or Lockdown (original post). (Lockdown is based on the open-source iAlertU.) You can arm and disarm both applications car-alarm style with your Apple Remote, and both use the motion detection system in any newer MacBook to set off the alarm if someone moves your laptop. The alarm also sounds with any movement of your mouse, keyboard activity, and more. Whenever the alarm is triggered, your MacBook’s iSight camera snaps a picture and can send it to any email address. Alternately, you can also automatically upload iAlertU pics to your FTP server if you’d prefer that to email.
If your laptop has a webcam, turning it into a backed-up security camera while you’re away can also help if your laptop were to get stolen. On Windows, you can install and run a free tool like Yawcam (original post) to turn your webcam into a motion-sensing security camera that can back up pictures it snaps to an FTP server. Just switch on Yawcam whenever you step away from your computer. On a Mac, you could try out Gawker, a killer open-source time-lapse application. You’d need to figure out a method for off-site backup with Gawker, but a method similar to backing up iAlertU pictures via FTP should do the trick. For more, check out my previous guide to using Gawker.
If worse comes to worst and your laptop is stolen, you’re still not without recourse. Several tools are available to help you not only track your laptop and the thief after your laptop has been stolen, but also to secure data on your computer after it’s been stolen.  Windows users should check out the free application LaptopLock. Here’s how to use Laptop Lock to report your computer missing, remotely delete or secure files, run programs, and even send a message to the thief.
Windows users should check out the free application LaptopLock. Here’s how to use Laptop Lock to report your computer missing, remotely delete or secure files, run programs, and even send a message to the thief.
Similarly, the cross-platform Adeona is an open source application designed to help you track a stolen laptop by gathering information like IP addresses and access point information (like the name of the hotspot the laptop is connected to). As an added bonus for Mac users, Adeona can also snap photos with your iSight whenever it tracks the thief’s location and upload that photo as well—a killer option for getting several pictures of the thief and possibly some information to determine where he/she is using your laptop.  With tracking tools like Adeona or LaptopLock, you’re not guaranteed pinpoint accuracy by any means, but it is a start. Adeona does not geolocate IP addresses itself, either, but you can plug the addresses or wireless networks the application sends to you into web-based tools like Wigle or the GeoIP demo to see what you can find. If you’re using LaptopLock on a Windows computer, the LaptopLock service can do the IP mapping itself.
With tracking tools like Adeona or LaptopLock, you’re not guaranteed pinpoint accuracy by any means, but it is a start. Adeona does not geolocate IP addresses itself, either, but you can plug the addresses or wireless networks the application sends to you into web-based tools like Wigle or the GeoIP demo to see what you can find. If you’re using LaptopLock on a Windows computer, the LaptopLock service can do the IP mapping itself.
 Since the sensitive information your computer holds is ultimately more important than your laptop itself, do yourself a huge favor by encrypting your hard drive. We’ve already walked you through how to encrypt your drive with TrueCrypt, a free and cross-platform encryption tool that protects your data in case of theft, so that’s the perfect starting point. If you’ve set up remote services on your computer—like SSH, VNC, or even an FTP server—you might want to consider using the DynDNS web service as a LoJack, to connects to your computer no matter where it’s located and backup or delete sensitive files if it is stolen.
Since the sensitive information your computer holds is ultimately more important than your laptop itself, do yourself a huge favor by encrypting your hard drive. We’ve already walked you through how to encrypt your drive with TrueCrypt, a free and cross-platform encryption tool that protects your data in case of theft, so that’s the perfect starting point. If you’ve set up remote services on your computer—like SSH, VNC, or even an FTP server—you might want to consider using the DynDNS web service as a LoJack, to connects to your computer no matter where it’s located and backup or delete sensitive files if it is stolen.  As a bonus tip, consider installing tracking software on your USB devices—like iPods or thumb drives—with previously mentioned application iHound. iHound works similarly to the laptop tracking and recovery tools mentioned above, but it places an enticing passwords.txt file on your USB drive’s root directory that uploads information like IP addresses when the thief opens that file.
As a bonus tip, consider installing tracking software on your USB devices—like iPods or thumb drives—with previously mentioned application iHound. iHound works similarly to the laptop tracking and recovery tools mentioned above, but it places an enticing passwords.txt file on your USB drive’s root directory that uploads information like IP addresses when the thief opens that file.
None of these methods are foolproof. A thief could cut your lock, run off with your laptop even with an alarm sounding, and format your hard drive immediately. As a rule of thumb, however, a lot of would-be thieves either don’t necessarily know how to do some of these things or simply don’t take the effort. Similarly, tracking and retrieval tools aren’t a sure thing. IP address mapping is inexact at best, and it’s often very difficult to use an IP address to identify anyone anyway. Every bit counts, though, even if it only means the difference between the thief making off with your laptop or your entire identity. If you’ve got your own methods for setting up a laptop security system—even if it just entails carrying it with you at all times—let’s hear about it in the comments. Adam Pash is a senior editor for Lifehacker who dreams of the day his laptop can return to him like an AT-5000 Auto-Dialer (but with better wheels). His special feature Hack Attack appears every Tuesday on Lifehacker. Subscribe to the Hack Attack RSS feed to get new installments in your newsreader.
Source : lifehacker
What happens when you want to just want a bunch of phones in your business, hotel, or organization and you don’t need a bunch of fancy and complicated features on the phone? It’s simple, just get a bunch of cheap analog phones. But how do you build a phone system to support a bunch of analog phones? It’s simple, just get a PBX (Private Branch Exchange) with a few FXS interfaces to plug in the phones. Just to rehash what an FXO and FXS phone port is and what the differences are, here’s a text representation how these devices are connected:
But this is where the tricky part comes in since your typical IP PBX which is essentially a computer doesn’t have any FXS interfaces so that’s where channel banks come in. A channel bank traditionally converts a T1 PRI interface in to 24 separate channels for 24 phone lines. The problem with traditional channel bank is not that they’re all that expensive, but the fact that they require a T1 PRI interface on the PBX for every 24 phone lines which are very expensive and cumbersome.
To get around this problem of having to use expensive T1 cards that are tied to a single server, Xorcom shuns T1 cards and uses good old USB 2.0 for its interface to the PC. Pictured below are some Astribank products with FXO or FXS ports along with the option for PRI ports. You just plug in your TBX to one of the Astribanks via one of the abundant USB 2.0 ports and you’re done. Simply plug it in to a USB 2.0 switch and two cheap open-source PBX appliances and you can instantly flip between the two servers in case one of them goes down for whatever reason. Any problems with one PBX server and you simply need to flip the USB switch and the other PBX is instantly lit up with all of its FXO and FXS ports. Trying to swap a PCI card with a T1 interface is far more difficult.

Pictured above is the front view of three Xorcom Astribank models ranging from 8 to 32 ports with any mixture of FXO and FXS ports. Pictured below is the back of the units showing the power and USB port in the back. The larger models also have 50 pin breakout ports so you can use your existing breakout box if you chose to do it that way.

The next two photos show all-in-one appliances designed to run Asterisk or Asterisk distributions from popular vendors like Trixbox or some other Asterisk derivative.


Today we're going to run down, step-by-step, how to crack a Wi-Fi network with WEP security turned on. But first, a word: Knowledge is power, but power doesn't mean you should be a jerk, or do anything illegal. Knowing how to pick a lock doesn't make you a thief. Consider this post educational, or a proof-of-concept intellectual exercise.
Dozens of tutorials on how to crack WEP are already all over the internet using this method. Seriously—Google it. This ain't what you'd call "news." But what is surprising is that someone like me, with minimal networking experience, can get this done with free software and a cheap Wi-Fi adapter. Here's how it goes.
 Unless you're a computer security and networking ninja, chances are you don't have all the tools on hand to get this job done. Here's what you'll need:
Unless you're a computer security and networking ninja, chances are you don't have all the tools on hand to get this job done. Here's what you'll need:
To crack WEP, you'll need to launch Konsole, BackTrack's built-in command line. It's right there on the taskbar in the lower left corner, second button to the right. Now, the commands.
First run the following to get a list of your network interfaces:
airmon-ng
The only one I've got there is labeled ra0. Yours may be different; take note of the label and write it down. From here on in, substitute it in everywhere a command includes (interface).
Now, run the following four commands. See the output that I got for them in the screenshot below.
airmon-ng stop (interface)
ifconfig (interface) down
macchanger --mac 00:11:22:33:44:55 (interface)
airmon-ng start (interface)
 If you don't get the same results from these commands as pictured here, most likely your network adapter won't work with this particular crack. If you do, you've successfully "faked" a new MAC address on your network interface, 00:11:22:33:44:55.
If you don't get the same results from these commands as pictured here, most likely your network adapter won't work with this particular crack. If you do, you've successfully "faked" a new MAC address on your network interface, 00:11:22:33:44:55.
Now it's time to pick your network. Run:
airodump-ng (interface)
To see a list of wireless networks around you. When you see the one you want, hit Ctrl+C to stop the list. Highlight the row pertaining to the network of interest, and take note of two things: its BSSID and its channel (in the column labeled CH), as pictured below. Obviously the network you want to crack should have WEP encryption (in the ENC) column, not WPA or anything else.
 Like I said, hit Ctrl+C to stop this listing. (I had to do this once or twice to find the network I was looking for.) Once you've got it, highlight the BSSID and copy it to your clipboard for reuse in the upcoming commands.
Like I said, hit Ctrl+C to stop this listing. (I had to do this once or twice to find the network I was looking for.) Once you've got it, highlight the BSSID and copy it to your clipboard for reuse in the upcoming commands.
Now we're going to watch what's going on with that network you chose and capture that information to a file. Run:
airodump-ng -c (channel) -w (file name) --bssid (bssid) (interface)
Where (channel) is your network's channel, and (bssid) is the BSSID you just copied to clipboard. You can use the Shift+Insert key combination to paste it into the command. Enter anything descriptive for (file name). I chose "yoyo," which is the network's name I'm cracking.

You'll get output like what's in the window in the background pictured below. Leave that one be. Open a new Konsole window in the foreground, and enter this command:
aireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:55 -e (essid) (interface)
Here the ESSID is the access point's SSID name, which in my case is yoyo. What you want to get after this command is the reassuring "Association successful" message with that smiley face.

You're almost there. Now it's time for:
aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 (interface)
Here we're creating router traffic to capture more throughput faster to speed up our crack. After a few minutes, that front window will start going crazy with read/write packets. (Also, I was unable to surf the web with the yoyo network on a separate computer while this was going on.) Here's the part where you might have to grab yourself a cup of coffee or take a walk. Basically you want to wait until enough data has been collected to run your crack. Watch the number in the "#Data" column—you want it to go above 10,000. (Pictured below it's only at 854.)
Depending on the power of your network (mine is inexplicably low at -32 in that screenshot, even though the yoyo AP was in the same room as my adapter), this process could take some time. Wait until that #Data goes over 10k, though—because the crack won't work if it doesn't. In fact, you may need more than 10k, though that seems to be a working threshold for many.

Once you've collected enough data, it's the moment of truth. Launch a third Konsole window and run the following to crack that data you've collected:
aircrack-ng -b (bssid) (file name-01.cap)
Here the filename should be whatever you entered above for (file name). You can browse to your Home directory to see it; it's the one with .cap as the extension.
If you didn't get enough data, aircrack will fail and tell you to try again with more. If it succeeds, it will look like this:
 The WEP key appears next to "KEY FOUND." Drop the colons and enter it to log onto the network.
The WEP key appears next to "KEY FOUND." Drop the colons and enter it to log onto the network.
With this article I set out to prove that cracking WEP is a relatively "easy" process for someone determined and willing to get the hardware and software going. I still think that's true, but unlike the guy in the video below, I had several difficulties along the way. In fact, you'll notice that the last screenshot up there doesn't look like the others—it's because it's not mine. Even though the AP which I was cracking was my own and in the same room as my Alfa, the power reading on the signal was always around -30, and so the data collection was very slow, and BackTrack would consistently crash before it was complete. After about half a dozen attempts (and trying BackTrack on both my Mac and PC, as a live CD and a virtual machine), I still haven't captured enough data for aircrack to decrypt the key.
So while this process is easy in theory, your mileage may vary depending on your hardware, proximity to the AP point, and the way the planets are aligned. Oh yeah, and if you're on deadline—Murphy's Law almost guarantees it won't work if you're on deadline.

Hacker is a tool used by the FBI to investigate / track the cracker who attack or harmful action in the world, I do not try, because it is lazy like hacking again, but if the friend - have friends who want to learn hacking or hacking attempts would only please to try, this hacking tool does not need to install the application in portable,
This is a package of 11 useful tools used to investivate the computer, it is used by most of the investigating agency including the FBI to inspect, hack and analyze other computers. For most of the programs, there is no need to install them, they are portable.
This download includes:
- ADS Locator (Alternate Data Streams)
- Disc Investigator 1.4 (File-Slack-Analyze)
- Historian 1.4 (Browser Analyze)
- Live View 0.6 (System Analyze)
- MUI Cacheview 1.00 (Registry Analyze)
- Networkminer 0.85 (Network Analyze)
- Regripper 2.02 (Registry Analyze)
- Systemreport 2.54 (PC Analyze)
- USB-History R1 (USB-Stick-Analyze)
- Windows File Analyzer (File Analyze)
- Winpcap 4.02 (Network

Windows Admin Hack allows you to reset the administrator password on Windows 2000 & XP.
You can reset your XP Password with this program.
Just Burn and Boot with CD.
File size: 2.63 MB
Download link : http://www.megaupload.com/?d=FFRPFXKB
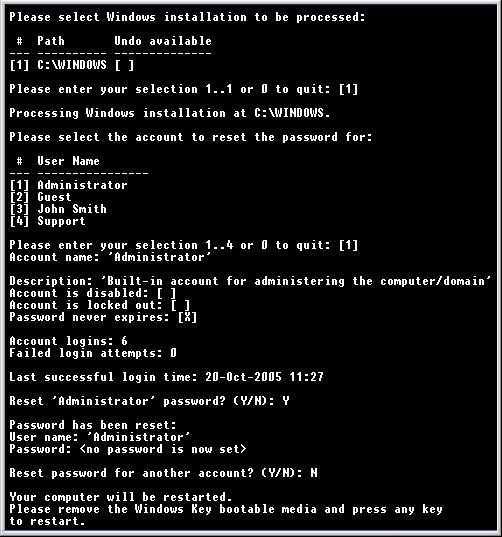
This program serves to reset the password acount in windows if we forget the password, the program is executed when windows booting the first time.
It is an ISO. This you burn a CD with eg Nero
[*]100% recovery rate
[*]Windows Vista supported
[*]All passwords are reset instantly
[*]Resets passwords with a bootable CD-ROM, USB drive or driver floppy
[*]Resets local policy settings
[*]Resets secure boot options: startup password or startup key disk
[*]Displays account properties
[*]Supports all Service Packs
Download Program Reset any Windows account password
http://rapidshare.com/files/193366363/Windows-Key-Enterprise-V7.9.2141.rar
Only 5 Mb



 Recover PDF Passwords and Instantly Remove PDF Restrictions
Recover PDF Passwords and Instantly Remove PDF Restrictions Get access to password-protected PDF files quickly and efficiently! Instantly unlock restricted PDF documents by removing printing, editing and copying restrictions! Advanced PDF Password Recovery recovers or instantly removes passwords protecting or locking PDF documents created with all versions of Adobe Acrobat or any other PDF application.
 LifeHacker has a nice piece called LifeHacker Top 10: USB thumb drive tricks. Some of the instructions could be a little better, and they should include some more screenshots, but this is definitely worth a look.
LifeHacker has a nice piece called LifeHacker Top 10: USB thumb drive tricks. Some of the instructions could be a little better, and they should include some more screenshots, but this is definitely worth a look.The tricks are:
What are some other cool tricks you can do with a USB flash drive? Join the discussion.


These days Broadband connections are very common...
As a result we are always connected... this annoys the ISP's !
Recently, I made some changes in my internet connection and faced the following problem and came out with a solution...
***** Problem *****
ISPs(Internet Service Providers) automatically disconnects the connection after some time in case of absolute inactivity. This reduces the load on their servers.
But...
This is irritating for the user, as he has to login every now and then...
Now, Imagine you are reading an article and after 10 mins.. as you turn to next page...? It asks you to Login..??? Now... that's crazy... isn't it ?
***** Solution *****
I coded an application that keeps the connection alive ! Basically it maintains little activity and prevents it from logging out. This is tested to be safe.. so no worries.
-------------------------------------------------------------
Application : Keep_Alive
Size : 40 KB
It uses : 128 bytes every 5 min. (i.e. 36KB in 1 day)
Link : Download Here
-------------------------------------------------------------
***** How To Use *****
> Double-Click the application(Keep_Alive)
> The Application runs in hidden mode, i.e. it will disappear and run in background
> You are done.. Now your connection will remain alive, forget about it.
-------------------------------------------------------------
But a Problem !
۩ On Restart the you again have to start the Application !!!
--------------------------------------------
Free PDF Editor
This is one completely free and simple PDF editing and creating software, it can help you to create your pdf documents by yourself in minutes.
No need any complex setting and knowledge about PDF format, handy and easy to use very much, specially for beginners. 
Free PDF Editor comes with a very intuitive GUI that is easy to understand even for the beginner users.
It is one WYSIWYG PDF builder, what you see is what you get, and you can insert text, image and shape, then drop, resize and move these PDF elements with your mouse.
Download and know more here http://www.freepdfeditor.net/
PDF Printer
PDF Printer 2009 is a comprehensive and professional utility designed to help you create PDF documents.
This enables virtually any Windows applications to create professional quality PDF documents - with just a push of a button!
With PDF Printer 2009, it is easy to create PDF documents from Word, Excel, PowerPoint, WordPerfect, Photoshop and other Windows applications. it natively supports over 300 file formats .
Download here PDF Printer
Windows XP Compatibility
So, you've upgraded to Windows XP or 2000 and now some of your old programs don't work. I hate that! It's been our experience that most older programs designed for Windows 95/98/ME will run on XP, regardless of what previous version of Windows they were originally designed for. The only ones that refuse to run are the ones you really, really need :-)
If you can't get a program to run on XP/2000, try this:
1. Right click its icon under the Programs menu, then select Properties from the resulting menu,
2. Now, click the Compatibility tab. You can choose what version of Windows you want XP to pretend to be.

For example, let's say you have a program that installs but refuses to run. If you set its compatibility for Win 98, you may find that it's now perfectly happy doing it's thing on XP (of course, it's blissfully ignorant of the fact it's been tricked).
This usually works about 50% of the time, so don't bet the preverbal farm on it.
Windows XP also has a "Program Compatibility Wizard" that will search for the best version of Windows to run a program under. To get there, click Start , Help and Support , then "Find compatible hardware and software for Windows XP", and finally, under "See Also" in the navigation pane, click Program Compatibility Wizard . You will be given instructions on what to do.
Another suggestion is to update your program. How often do you go to the website of a software manufacturer and look for program updates? What about updated drivers for your sound card? Most of the time you can download update patches for free!
With some luck, you will be playing your favorite old games or using that older software in no time.
~ Steve
Would you like to have one of your pictures as a desktop background? It's easier than you think!
1. Figure out your screen resolution. Before you begin, you'll need to figure out what size the final image needs to be. Fortunately, this is really easy. Just right-click a blank area on your desktop and select Properties from the resulting menu. Then, click the Settings tab on the resulting screen. Look at the Screen resolution area and write down the current setting.

2. OK, now you know the size you need, the next step is to pick a photo. So, head to your archives and open the photo you want to use in your favorite imaging program. I'll wait here.
3. Have the photo opened? Cool. Now, adjust anything that needs adjusted (color, saturation, etc). Now, you'll need to resize the image to match your monitor resolution. This setting varies by program, but it's usually found under the Edit or Image menu in most programs.
Most programs will have an option to "constrain proportions". This keeps the image proportional as you change sizes. Make sure this option is checked or the image may look distorted. For more on how this works, check out:
http://www.worldstart.com/tips/tips.php/1587
Now, here's the trick. You may find that when you resize the image with the proportions constrained, the numbers don't work out to match your screen resolution. If the numbers are close (say within 10 pixels), don't worry about it. Any distortion will be minimal. However, if you find the numbers are off by quite a bit, you'll need to either crop the image or put it onto a black background that is proportional to your screen resolution.
For the details on how to do this, check out our Constrain Proportions article (linked above). It will explain in detail how you can turn an image that's not proportional into one that is.
4. Once your have your image resized, cropped, and generally ready to go, save it as a JPEG. I'd put it in the "My Pictures" folder for easy reference, but the choice is yours.
5. Last step! Right-click your desktop, select Properties from the resulting menu, then go the Desktop tab. Click the Browse button and navigate to the image you just saved. Select it, hit OK and you should now have your photo set as your desktop wallpaper!
Happy wallpapering.
~ Steve
We all know that cell phones are one of today's big crazes. An even bigger one is camera cell phones. Before we know it, all cell phones will probably have camera abilities, because the world today likes to see real images rather than just words. So, it may be a good idea to know what you can do with the pictures you take on your phone after the shooting is done.
Picture Messaging
A common way that people transfer photos from their cell phones to their computers (that doesn't really have any additional cost from your regular monthly bill) is picture messaging. It works pretty much the same as text messaging; you just have to have text messaging enabled on your cell phone. If you don't, this method will not work.
Note: Expect this method to be a little different for various phone models, but the following directions are pretty basic and similar for all phones.
If you would like to send a picture to another person's cell phone or if you want to e-mail a picture to a friend or even to yourself, you just need to open your phone and go to the Menu. Find your phone's Media Gallery and then choose Pictures. At this point, you can pick the photo you'd like to send. Once you have it chosen, go to Options and choose Send in Message (like you're sending a text message). This is where you choose to send it to one of the Contacts listed in your phone or if you want to e-mail it to someone or yourself. Pick the person you're sending it to and push the OK button and then Send.
You can also send text with the picture if you want to do that. If you end up e-mailing the picture to someone, you will just have to type in their e-mail address and they will get it in their Inbox. You just need to make sure the person you're sending the picture to has picture capabilities too.
Data Cable
Another way you can transfer photos to other people is to put them directly onto your computer, so you can e-mail them to your friends or save them to a disk or a CD. So, to do that, you have to have some sort of a USB data connection kit, which comes with the cable cord that plugs your phone into your computer's USB port and the software that will help you in transferring the pictures from your phone. You usually have to purchase these kits separate from your phone. The store where you buy your phone should have them available and they will be able to tell you which one will work with your type of phone.
Once you have your phone and computer connected, you can start transferring the pictures. Again, keep in mind that these kits are phone specific, so you need to make sure that you get one that will be compatible with your phone model.
Bluetooth
Another way to handle the pictures on your cell phone that is becoming more popular every day is a wireless technology called Bluetooth. Bluetooth works with short-range wireless technologies that allow you to easily send photos from your phone to a laptop or desktop computer. The computer you are sending them to just has to be equipped to accept the pictures.
The most difficult (but it can sometimes be fairly easy) part about Bluetooth is matching the phone to the computer, so they are both compatible with each other. But, once that it is done, sending the images couldn't be easier.
As long as your phone has the Bluetooth software on it, you can send the images without any extra charges billed to you. You can also send photos to other Bluetooth users' phones without any wires or additional charges. This seems to be the most versatile way to go if you're looking to maybe spend a little more money up front for the Bluetooth works, but it will save you money in the long run when you don't have to pay any extra charges when sending your pictures back and forth.
Another way for you to send pictures between your friends and family is to e-mail them. Your cell phone has to have e-mail capabilities for this to work, but a lot of the phones these days come with that ability. You can e-mail them to other people or, as mentioned above, to yourself. You just have to type the e-mail address in the To: field just like you would if you were using Outlook Express and it will be sent.
If you see something while you're out and about that you just have to take a picture of, you can snap the photo on your phone, send yourself a quick e-mail and when you get home, the picture will be on your computer waiting for you. You can then send it off to other people or do something like set it as your desktop wallpaper.
Removable Memory Cards
Another new technology that is presenting itself with camera phones is an external memory card for your phone. The phone just comes with a slot for the card and you can transfer the shots to your computer in a snap. You will need to purchase an external memory card reader so it will all work, but it's one of the easiest ways to go if you takes several pictures with your cell phone.
When you have the card reader installed, you just remove the memory card from your phone, insert it into the reader and your computer will recognize it as another drive. You can then drag and drop the photos wherever you want them to go, e-mail them to others, etc. The options are pretty endless with this choice. You can then get rid of the existing pictures on your phone (since they're on your computer and not lost) and go out and take more. It's that easy!
Just one more reminder: all of these applications work differently with different phones, so make sure you refer to your phone's manual before doing anything you're not sure of. But, all in all, this is all really cool when you think about it. Who would have thought we could do so much with a little phone? Technology is just out of this world!
~ Erin
Hacks - Cracks - Tips - Tricks © 2008 by Hacks - Cracks - Tips - Tricks | Designed by Design Blog | Blogger Template by ThemeLib.com