FACEBOOK, TWITTER PROVIDE SENSITIVE INFORMATION FOR CORPORATE CRIMINALS


 Everyone who uses an Internet connection is downloading files from there. It can be automatic file transfers like downloading new emails or filling the browser cache when opening new websites but also manual downloads of pictures, videos or programs. The most dangerous type of downloads are program executables as they can infect a computer system easily if the user has no precautions in place. The following article will give users of every experience level some guidelines at hand on how to download and handle files that are downloaded from the Internet.
Everyone who uses an Internet connection is downloading files from there. It can be automatic file transfers like downloading new emails or filling the browser cache when opening new websites but also manual downloads of pictures, videos or programs. The most dangerous type of downloads are program executables as they can infect a computer system easily if the user has no precautions in place. The following article will give users of every experience level some guidelines at hand on how to download and handle files that are downloaded from the Internet.It all begins at a website or server. This is the starting point and it might be a good idea to start validating that server before even thinking about downloading files from there. This can be done manually by performing some searches in search engines but also automatically with browser add-ons or plugins like Web of Trust, McAfee’s Site Advisor and a plethora of other respected programs including local security software that can also check websites and servers.
The second step involves downloading the file to the local computer system. There is not a lot that can be done here in this step. The only defense are security software programs that are installed on the computer system that should scan the file and report back to the user if they believe it to be malicious. Cautious users can also use one of the many online virus scanners to upload the file and scan it online. Services like Virus Total scan the files with more than a dozen different up to date antivirus engines resulting in a more precise analysis of the file.
Another option is to check the hash values of the downloaded files to make sure that they have not been tampered with. This only makes sense if the developer is displaying the values on a trusted website.
It is pretty safe to assume that the file is safe and can be executed on the computer system if it did pass the tests. There is however a last step that can be done to add the extra mile of security: Virtualization. Programs like Sandboxie or VMWare Player make it possible to execute programs in a closed environment for testing purposes. The benefit of this approach is that they cannot harm the rest of the computer system if they should be malicious.
Windows XP and Windows 2003 administrators who are noticing difficulties like performance drops, application or system crashes while using the computer system that can be caused by third party applications that are overwriting shared system files of the operating system. System Administrators can run the sfc /scannow command to verify the integrity of all protected operating system files. The check will basically compare the current file with the original version and replace modified files with the original Microsoft version.
It has to be noted that the command will replace all modified files even those that have been modified deliberately by a user of the system (e.g. a patched uxtheme.dll file to be able to use third party themes).
Not everyone likes to use a command line version (that comes with several parameters) on the other hand. File Checker is a small portable software program that offers a GUI for the process. The program gives the system administrator the tools at hand to run most sfc commands from that GUI including starting a system scan, purging the cache or defining the locations of the setup sources.
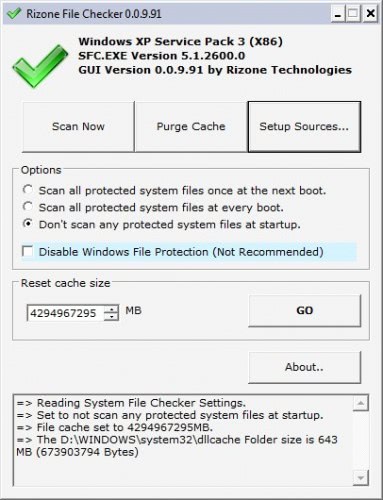
Options are available that can change the process further. It is possible to reset the cache size to a new value, to disable the Windows File Protection and to define how protected system files should be handled by the scan.
The Windows XP system file checker is a portable alternative for system administrators who like to work with graphical user interfaces. File Checker is available at the developer’s website.
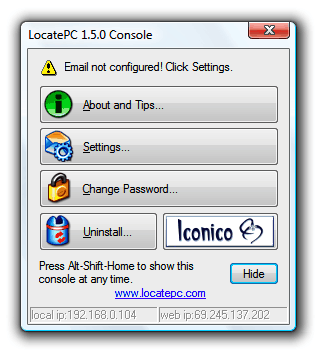
If you travel a lot chance is that you will eventually fall victim to theft. If you happen to have your notebook or laptop with you most of the time chance is pretty high that the thief will have the desire to steal that one. Chances are pretty slim that you will see your notebook again after the theft but you can increase them a bit by using Locate PC.
Locate PC only works if the thief is stupid enough to boot your computer while being connected to an internet connection. I cannot really say how many thiefs would do that but it can happen and that’s probably reason enough to use Locate PC. A slim chance is better than no chance at all, don’t you think ?
Locate PC (via Cybernet News) will send emails periodically whenever the PC is connected to the Internet, by default one email is send per day and another one for every IP change. The application is running in the background with an obscured filename and no system tray icon making it harder to identify. I would say that you do not need to worry about that though, if the thief really boots the PC while it is connected to the Internet then you should not fear that he will discover the little tracking application.
One thing that actually might work pretty well is to create a bogus account that does not require a password. I mean, a thief that gets a password prompt will probably not be able to load the operating system which would make the whole configuration void.
The emails that are send contain several interesting information, not only the IP that it is being send from. It displays the computer’s host name and logged in user. This will be probably your information though. More interesting are the network connections that are listed. A dialup connection would reveal the phone number and the user name which can lead directly to the thief.
A traceroute command is issued as well and identifying information are pulled from Windows. The important information that can lead to the thief are the IP address, the network connections and the traceroute command. Everything else will be your information unless the thief decides to chance the name and address of the owner to his own.
Download LocatePC
Hacks - Cracks - Tips - Tricks © 2008 by Hacks - Cracks - Tips - Tricks | Designed by Design Blog | Blogger Template by ThemeLib.com